What Is A Ransomware Attack And Who Are The Real Victims ?
Who are the real victims of Ransomware attacks.
Let’s take a deeper look at the ramifications of
corporations having you data held ransom.

James Scott
Senior Fellow - Institute for Critical Infrastructure Technology
“Ransomware is more about manipulating vulnerabilities in human psychology than the adversary’s technological sophistication“
The biggest meat processing company in the world joins the growing list of Ransomware victims..
Today the BBC are reporting the latest ransomware attack. To be honest the press is not very good at reporting this kind of attack and the scale and impact seems to be missed with the focus being on the more high profile, news worthy targets. This time it’s the largest meat processing company in the world, JBS, but who are the real victims of large scale ransomware attacks and how big a problem is it?
The biggest meat processing company in the world joins the growing list of Ransomware victims..
Today the BBC are reporting the latest ransomware attack. To be honest the press is not very good at reporting this kind of attack and the scale and impact seems to be missed with the focus being on the more high profile, news worthy targets. This time it’s the largest meat processing company in the world, JBS, but who are the real victims of large scale ransomware attacks and how big a problem is it?

We’ll start with an analogy as far from the digital world as we can get and 70 years in to the past…
What is ransomware and how does a ransomware attack work – the simple version?
Maybe we should start with what is ransomware and what is a ransomware attack.
“Ransomware is a piece of software or code that when executed makes a resource inaccessible until a ransom is paid for its release.”
We’ll start with an analogy as far from the digital world as I can get and 70 years in the past. 70 years ago all your company data would have been held as paper in filing cabinets. Let’s pretend that your filing cabinets are indestructible and locked with the best locks you can get. You building is locked and has an electric fence around it. Everything is safe and secure.
One day you get a parcel from one of your regular suppliers, nothing unusual just a regular brown box which is addressed to Joe in stores. Joe opens the box and out jumps the hacker who runs around your company putting all your filing cabinets inside his own super expanding impenetrable walk in safe which has a combination lock on it with a trillion, trillion combinations.
Some time later when you have realised that all your companies data is locked inside a box that can only be opened by the hacker, you get a friendly message asking for £10 million for the combination number.
So that is the basic principle of how it works from a non technical perspective.
What is ransomware and how does a ransomware attack work
– the more technical version?
A Cryptoviral extortion which is the technical term for a scam of this type is made up of three steps that are carried out between the attacker and the victim.
- [attacker→victim] The attacker generates a key pair and places the corresponding public key in the malware. The malware is released.
- [victim→attacker] To carry out the cryptoviral extortion attack, the malware generates a random symmetric key and encrypts the victim’s data with it. It uses the public key in the malware to encrypt the symmetric key. This is known as hybrid encryption and it results in a small asymmetric ciphertext as well as the symmetric ciphertext of the victim’s data. It zeroizes the symmetric key and the original plaintext data to prevent recovery. It puts up a message to the user that includes the asymmetric ciphertext and how to pay the ransom. The victim sends the asymmetric ciphertext and e-money to the attacker.
- [attacker→victim] The attacker receives the payment, deciphers the asymmetric ciphertext with the attacker’s private key, and sends the symmetric key to the victim. The victim deciphers the encrypted data with the needed symmetric key thereby completing the cryptovirology attack.
This summary is taken from the Ransomware article on Wikipedia and best explains in a concise manner the too and fro of the engagement between attacker and victim.
The malware is usually categorised as a trojan at this point as it is in the form of a link or attachment that is sent to the victim, either specifically for a precisely identified target , usually through a phishing/spear phishing campaign, or a more scatter gun approach. Either way the payload is pretending to be something of use or interest to the victim and falls into the category of being a trojan horse.
Since the Ransomware started to take hold back in 2012 there have been an increasing number of variants including :
|
Reveton |
2012 |
|
CryptoLocker |
2013 |
|
CryptoLocker.F and TorrentLocker |
2014 |
|
CryptoWall |
2014 |
|
Fusob |
2015 & 2016 |
|
WannaCry |
2017 |
|
Petya |
2017 |
|
Bad Rabbit |
2017 |
|
SamSam |
2016 |
|
Syskey |
2017 |
Who are the victims of Ransomware?
The initial thought would be that the victims are the businesses that are infected and this is true to some extent. From individuals to corporations the list is endless.
Blackfog have maintained a list of the larger and more high profile incidents in 2020 and are again compiling a list for 2021. I have to say it is well worth a read and contains some familiar names.
At the time of writing this article in June of 2021 we can see that there are certain sectors which are taking the brunt of these attacks, for whatever reason…
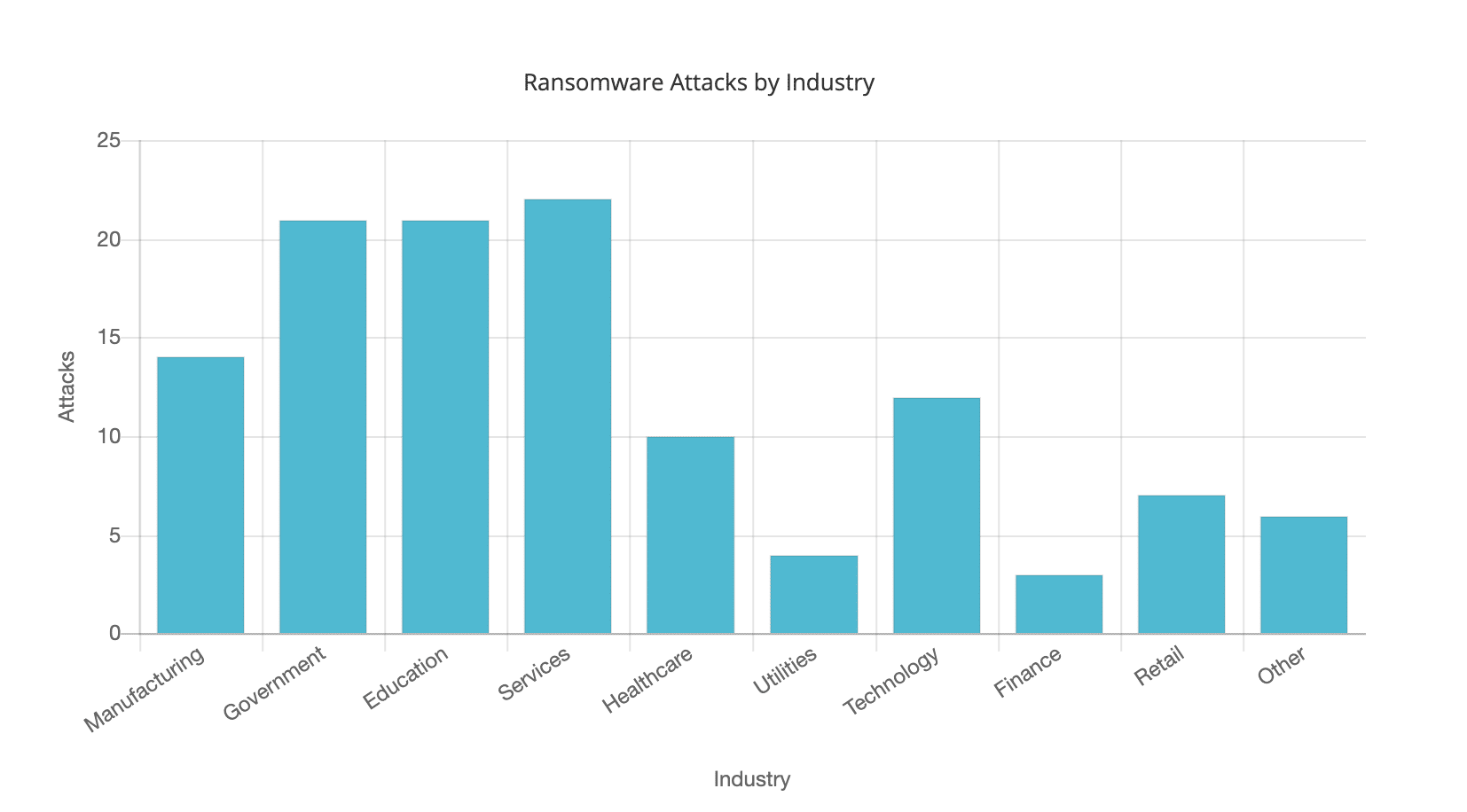
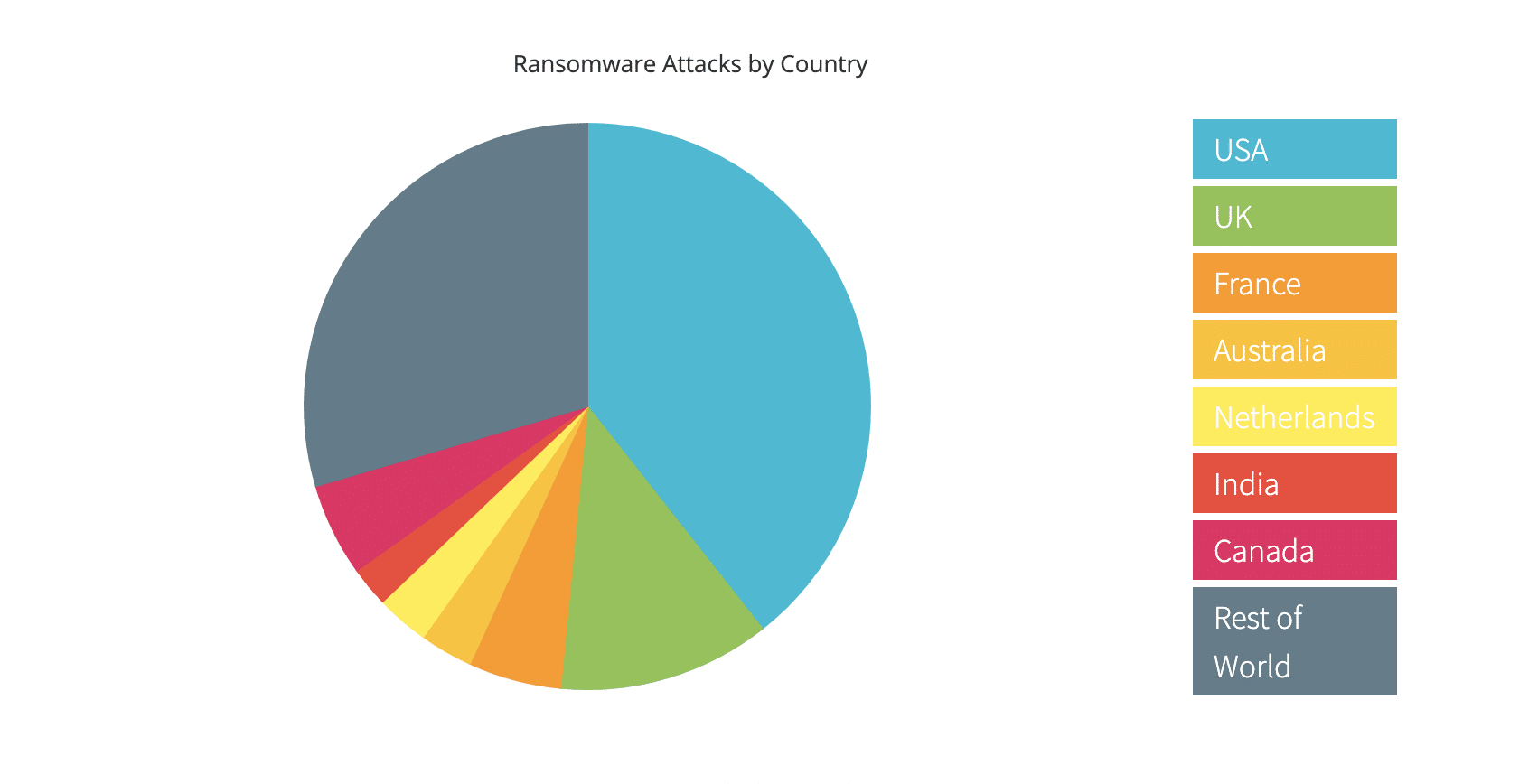
And there seems to be particular areas of the world that are again taking most hits..
Looking at the 2021 monthly figures it is plain to see that this is a problem that is getting bigger month on month and year on year.
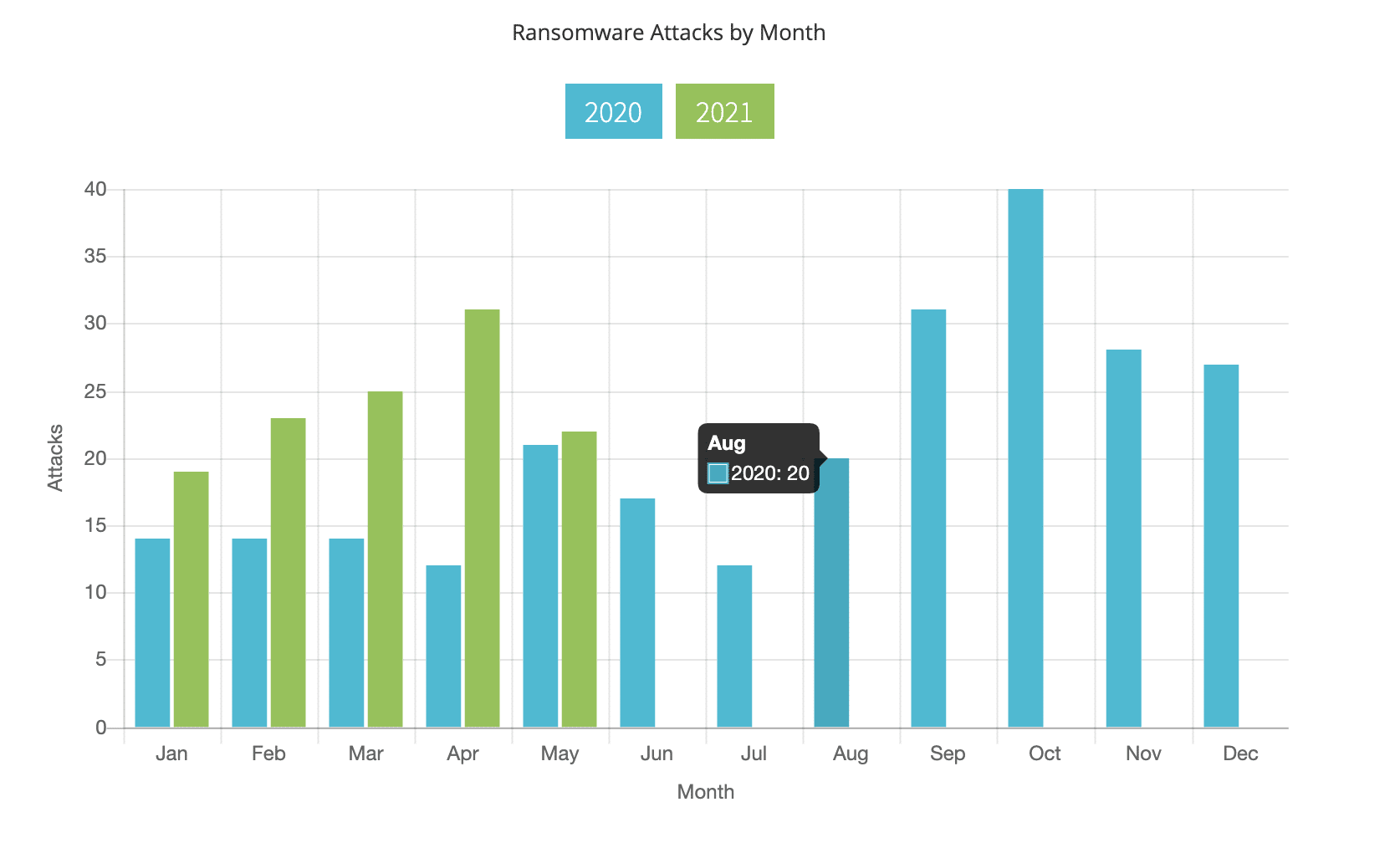
Credit needs to go to Blackfog for the data and reasearch above. Without this kind of research it would be impossible to both track the impact of ransomware and also to understand how to fight it…. Thanks Blackfog.
The real victims of Ransomware.
It is quite easy to look at ransomware and the massive payments that are made to attackers to either recover data or stop it being posted to the internet and think that they are the victims, but I’d like to take a look at just a couple of incidents that have been in the news recently and delve a little deeper…
Who turned off the gasoline tap?
Colonial Pipeline is one of the largest fuel pipelines in the US. They eventually paid over a ransom of $5 million to the DarkSide ransomware gang, but the attack didn’t stop the pipeline from working. The panic and fuel shortages that occurred were in fact due to Colonial Pipeline shutting off the pipeline themselves. In fact the systems that were compromised were part of the companies billing systems. They decided to shut down their systems because without the billing systems operating they had no way of knowing who they were sending the fuel to and would not be able to place accurate bills for their clients. As a result there were scenes of people panic buying and filling plastic bags with petrol. Shortage drove up prices, that the average motorist had to pay to keep their vehicle on the road – I would guess that collectively the public in 7 US states paid more that the $5 million that made up the ransom figure.
We serve and protect you personal data.
Staying in the US as they have the highest incidence of published ransom attacks, the Azusa Police Department in Southern California became a victim of the DoppelPaymer criminal gang who stole data before following up with a ransom demand. Officials of the city of 48,000 residents decided to keep the attack a secret for 2.5 months before disclosing that data compromised in the attack “may have included” Social Security numbers, driver’s license numbers, medical information, financial account information and other records. The cybercriminals posted 7 GBs of Azusa records on the Dark Web. In this case it looks like the Police Dept didn’t pay out, it would have been hard for them to do so, but the citizens of Azusa certainly paid a hefty price.
The waiting list gets longer.
Healthcare is always a sector that can be hard hit by the repercussions of any kind of attack, after all peoples lives can be put at risk through no fault of their own. The Health Service Executive in Ireland posted on Twitter that they had experienced a “significant ransomware attack which forced the shutdown of their systems as precaution and all outpatient appointments were cancelled.” A ransom at $20 million was demanded in exchange for decrypting the data and deleting 700GB of unencrypted files that they had stolen during the attack. In this case hospital appointment were cancelled and other procedures delayed on top of all the delays from the Covid-19 pandemic
In conclusion, Ransomware is becoming an increasing problem for businesses and IT professionals. However as a business we need to think about the additional impact of such events including to our business continuity, reputation and most of all our customers in whatever shape they come.
Now we know a little more about how Ransomware works it leaves us with the big questions, “What is the best ransomware protection?” and “What is the best way to resolve a ransomware attack?” For the answers and more out our blog “How do you avoid or recover from a Ransomware attack?“